Friday Night Dinner: Sunday in Brooklyn
James Street is full of restaurants. It's near Oxford Street and Bond Street, so an excellent place to enjoy a meal after a hard day of shopping, if that's your thing. We hadn't done any shopping, but after a week at work, a relaxing dinner is always welcome.
Sunday in Brooklyn is their second venue — their first one is in Notting Hill — and styled after a Brooklyn Brunch spot. So good for breakfast (weekdays) and brunch, but they also serve dinner in the evening.
We were seated in the front room with a bunch of other pairs of diners. The vibe was relaxed. The menu is fairly extensive with starters, salads, Italian plates, burgers, and mains. We weren't overly hungry, so picked the corn ribs to share as a starter. These were cut into quarters, slightly crispy, and were served with a slightly underwhelming peanut-flavoured dip (it wasn't really necessary as the corn ribs were delicious by themselves). They weren't the easiest to eat — fingers required — but yet very tasty.
For her main, my wife selected the flame grilled salmon. This came with a smashed avocado and pineapple salsa. Although tasty, the salsa being cold, whilst the salmon was hot, was a little odd. On the side, she also had a green bean and almond side, which worked better with the fish than the cold salsa. I had the grilled sirloin steak, with a peppery three pepper sauce, and served with a side of crispy and garlicky fries.
After our mains, we did have a look at the dessert menu, but opted against it. Even though our waitress was highly recommending having the Sunday Pancake™ that they're apparently famous for. We were too full— maybe something to try another time.
We enjoyed our Friday meal at Sunday in Brooklyn, and perhaps we should come back and have an actual brunch, and then also try their signature pancakes.
Xdebug Update: January 2026
In this update I explain what happened with Xdebug development in the last month.
In the last month, I spent only around 9 hours on Xdebug, with 24 hours funded. The rest of the time, I spend on building out Xdebug Cloud version 2.
Xdebug 3.5
Most of this month I spent on a few bug and performance reports from the Xdebug 3.5 release — most notable a performance degradation on Windows due to the new experimental control sockets.
I also spent time on my large better code coverage patch, which still isn't quite as performant as the current feature; although it does give more precise results.
Native Path Mapping
Fabian Potencier, from Symfony fame, has created an exploratory patch for Twig to make use of Xdebug's new Native Path Mapping functionality.
From the initial patch, it became clear that a few things need to be improved on the Xdebug side for this to be a complete feature. For that reason, I have created a few issues to work on:
My PhpStorm issue to allow for the setting of breakpoints in template file has now been merged, and is scheduled for 2026.1 EAP 2. At the time of writing this isn't quite out yet, so I will keep you posted.
Xdebug Videos
I have created one new videos in the last month:
All Xdebug videos are now available on the phpc.tv PeerTube instance. This will be the primary location for new videos, although I also still post them to my YouTube channel.
If you have any suggestions, feel free to reach out to me on Mastodon or via email.
Xdebug Cloud
I am currently reworking Xdebug Cloud, the Proxy As A Service platform to allow for debugging in complex networking scenarios.
The new version will allow for automatic subscriptions.
Packages will start at £16/month for one-developer companies.
If you want to be kept up to date with Xdebug Cloud, please sign up to the mailing list, which I will use to send out an update not more than once a month.
Shortlink
This article has a short URL available: https://drck.me/xdebug-25oct-k48
Friday Night Dinner: The Porter's Table
The Porter's Table is part of the massive new Guinness Open Gate London development, which features a brewery and tour, a beer garden, and several restaurants. They have a different approach to the original Open Gate in Dublin, where they mostly try out new beers on unsuspecting punters.
Where Gilroy's Loft specialises in seafood, The Porter's Table is focussed on grilling vegetables, fish, and meat. And of course there is a fair amount of different beers to sample as well.
After finding the restaurant, we soon got ourselves one of those while looking over the menu.
We originally only chose the frickels as our starter (beer-batter deep-friend cornichons), but after realising that we didn't have any vegetables with our mains, we decided to add the seasonal Brussels sprouts. When these came (after the frickels, and before the mains), we were glad that we did. They were prepared with beetroot and orange, which made for a delightful combination.
For her main, my wife had the butcher's skewer; lovely cubes of rib-eye, marinated, and grilled on a skewer with red peppers, tomatoes, and red onion slices. I had the pork chop, which came with half a roasted bulb of garlic, cut through horizontally. I enjoyed prising the sweet roasted cloves of garlic flesh out of the papery skin. My meal was seasoned, and nicely moist. We ordered some chips on the side, which were crisp and fluffy. The serving of mayonnaise was too small, but I nearly always find that his the case.
The food was nice, but the service was quite haphazard. Orders went slightly wrong, and were offered food that we hadn't ordered — nor did the tables next to us.
We'll likely return to the Open Gate, but probably to try Gilroy's Loft (the seafood restaurant), or the beer garden with food truck later in the year when the weather is much improved.
Shortlink
This article has a short URL available: https://drck.me/porters-table-k41
Life Line
Updates from walk
Created a waste_basket, an information, and a grit_bin; Updated 2 bicycle_parkings
Created 8 waste_baskets; Updated 3 benches and 3 waste_baskets
If I would like (to rent) a desk for working for an afternoon in Amsterdam North, or near Centraal, what would be a good place?
Updated a marina
I walked 9.7km in 1h46m04s
Updated an information and a bench
Created 2 benches
Created 4 picnic_tables, a bench, and a fitness_station; Updated a pub and a sport club
Created 2 benches and 2 waste_baskets; Updated 4 benches, a bus_stop, and a cafe; Confirmed a dentist
Created 3 waste_baskets, 2 main entrances, and a bench; Deleted a cycle_barrier, a bench, and a waste_basket
Created an information; Updated a waste_basket and a bench
Updated 2 waste_baskets and a bench
Created 3 benches
Created a waste_basket; Updated 2 benches and a tree
I hiked 17.0km in 3h52m14s
I walked 3.5km in 35m31s
Created a main entrance and a home entrance
Created an entrance
Updated a house building
Created an entrance
I walked 5.8km in 1h15m06s
I've just finished reading "A Cheese-Monger's Tour de France", by Ned Palmer.
Now I want to try many of those! 🧀
I'm thrilled to announce that I'll be speaking at the 23rd edition of #phpday, the international PHP conference in Italy, organised by @grusp.
I’ll be presenting a talk titled: "Better Debugging With Xdebug".
It's in Verona, Italy, on May 14-15th 2026.
You can use my speaker’s discount code "speaker_10OFF" for 10% off at https://www.phpday.it/tickets/?utm_medium=organic&utm_source=linkedin&utm_campaign=post-speaker
I walked 5.5km in 1h11m00s










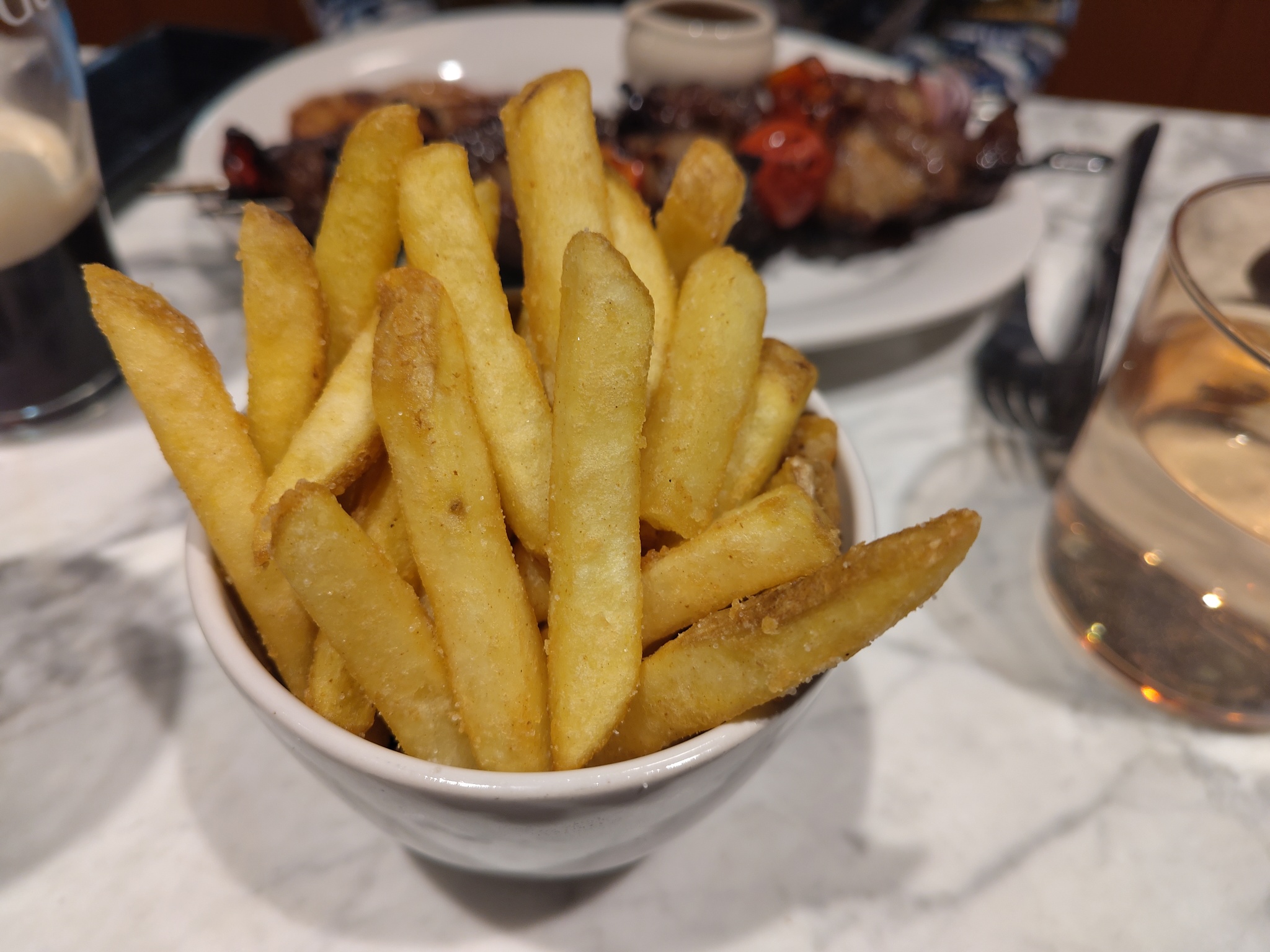


Shortlink
This article has a short URL available: https://drck.me/sunday-in-brooklyn-k4b